1. Introduction
Wireless networks are integral to modern communication. From homes and offices to public spaces, Wi-Fi offers unparalleled convenience. However, with convenience comes vulnerability. If a wireless network isn't properly secured, it can become an easy target for attackers.
Kali Linux, a Debian-based Linux distribution designed for penetration testing and digital forensics, includes a suite of tools ideal for assessing wireless network security. This article explores how to ethically and legally test wireless networks using Kali Linux. These methods are intended for educational purposes only and must be used only on networks you own or have explicit permission to test.
2. Legal & Ethical Considerations
Before diving into wireless testing, it’s crucial to understand the legal landscape. Unauthorized access to networks—even for the sake of “testing”—is illegal in most jurisdictions and violates ethical hacking principles.
Always ensure:
-
You have explicit permission to test the network.
-
You document your testing process.
-
You report findings to the network owner in a responsible manner.
3. Kali Linux Overview
Kali Linux is widely used in cybersecurity due to its built-in tools, updated repositories, and active community support. It comes pre-installed with tools specifically designed for:
-
Network scanning
-
Packet analysis
-
Wireless exploitation
-
Password cracking
For wireless testing, some of the most important tools include:
-
Aircrack-ng
-
Reaver
-
Wifite
-
Wireshark
-
Kismet
4. Wireless Adapter Requirements
Most built-in laptop Wi-Fi cards do not support monitor mode or packet injection, which are essential for wireless testing. It’s recommended to use USB wireless adapters such as:
-
Alfa AWUS036NHA (Atheros chipset)
-
Alfa AWUS036ACH (Realtek chipset, requires drivers)
Make sure your adapter supports:
-
Monitor Mode: allows listening to all traffic on a channel
-
Packet Injection: allows sending customized packets
5. Popular Wireless Testing Tools in Kali Linux
a. Aircrack-ng
A powerful suite of tools for monitoring, attacking, testing, and cracking Wi-Fi networks.
b. Reaver
Targets WPS vulnerabilities in WPA/WPA2 routers.
c. Wifite
An automated tool that wraps around Aircrack-ng and Reaver to perform attacks easily.
d. Wireshark
Used for packet analysis and deep inspection of network traffic.
e. Kismet
A wireless network detector and sniffer useful for detecting hidden networks.
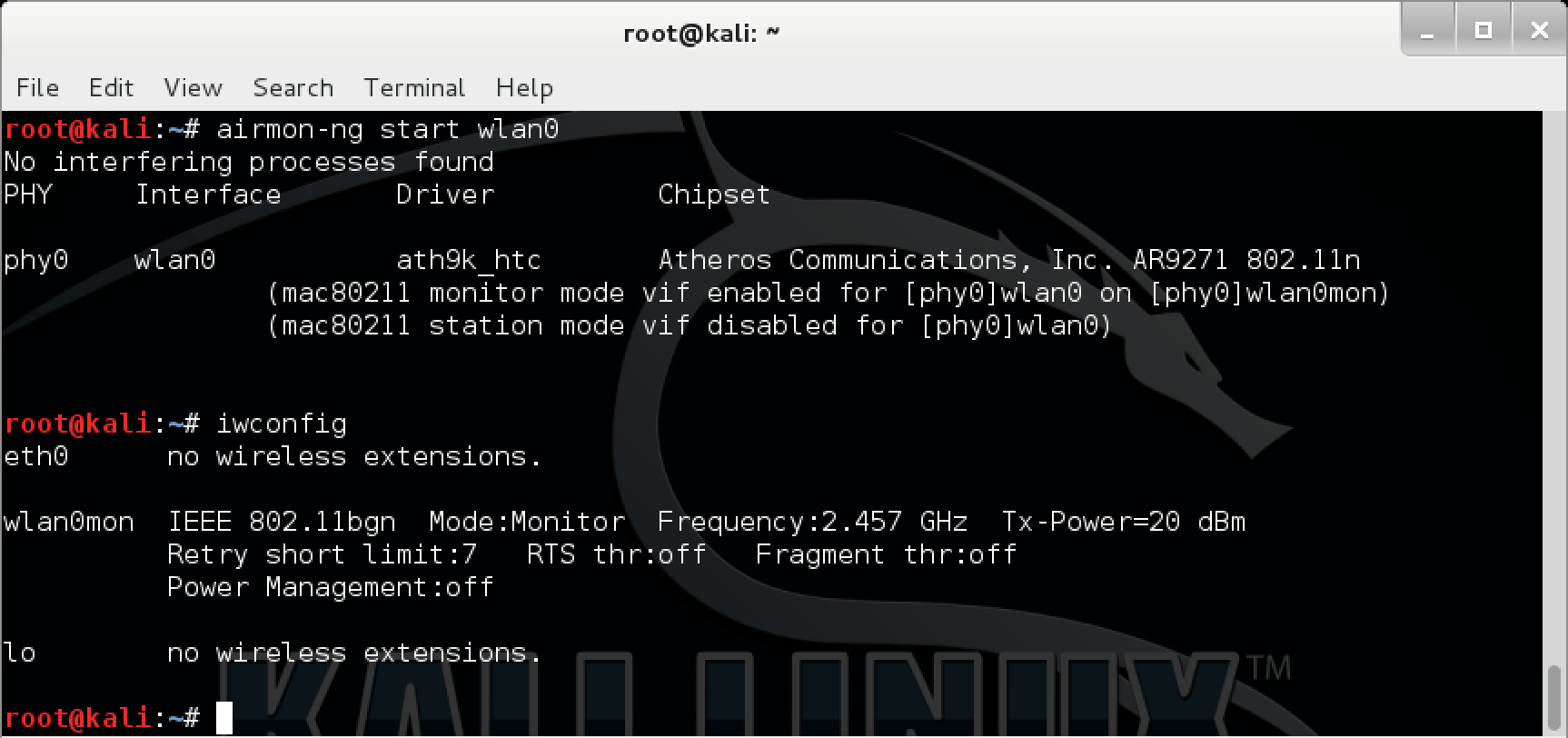
6. Enabling Monitor Mode
To perform tests, you must place your wireless adapter into monitor mode:
This creates a monitor interface (e.g., wlan0mon). You can now capture all wireless traffic.
7. Encryption Types: WEP vs WPA/WPA2
Understanding encryption is key:
-
WEP: Easily cracked, outdated.
-
WPA/WPA2: More secure, uses a handshake for authentication.
-
WPA3: Newer standard, more resistant to brute-force attacks.
Testing should focus on WPA/WPA2 as WEP is largely obsolete.
8. Capturing WPA/WPA2 Handshake
To crack a WPA/WPA2 password, you must capture a 4-way handshake. Use airodump-ng:
Identify the target network (SSID and BSSID). Then focus on it:
To force a device to reconnect (to capture handshake), deauthenticate it:
If a device reconnects, a handshake will be captured.
9. Cracking the Password with Aircrack-ng
Once you have the handshake:
Aircrack-ng uses a wordlist to brute-force the password. Kali includes default wordlists like rockyou.txt.
10. Using Wifite for Automated Testing
To automate much of the process, use Wifite:
Wifite automatically detects vulnerable networks, captures handshakes, and attempts to crack them.
11. Packet Analysis with Wireshark
Wireshark allows you to:
-
Analyze captured packets
-
Inspect authentication frames
-
Detect suspicious traffic
Use it to inspect *.cap files generated by airodump-ng:
Look for EAPOL frames indicating a WPA handshake.
12. MAC Spoofing and Deauthentication (For Defense Simulation Only)
To test MAC filtering or simulate how an attacker might hide, spoof MAC addresses:
To simulate a deauthentication attack (for testing detection systems):
These techniques should only be used in controlled lab environments.
13. Defensive Measures
How to protect your network:
-
Use WPA3 encryption if supported.
-
Disable WPS (it’s highly vulnerable).
-
Use strong passwords (avoid dictionary words).
-
Change default router settings.
-
Monitor connected devices regularly.
-
Use MAC filtering cautiously (easy to spoof but adds a layer).
14. Conclusion
Wireless network testing with Kali Linux provides invaluable insights into the strengths and weaknesses of your Wi-Fi setup. With powerful tools like Aircrack-ng and Wifite, you can ethically simulate real-world attacks to better defend your infrastructure.
Always remember: ethical hacking is about protection through understanding. Learn the methods attackers use, so you can stop them before they start.