Introduction
Aircrack-ng is one of the most powerful tools in the cybersecurity world for auditing wireless networks. Bundled in Kali Linux, this suite is widely used by penetration testers and network security experts to test the security of Wi-Fi networks, specifically WPA and WPA2 encryption. The suite includes a range of tools for monitoring, attacking, testing, and cracking Wi-Fi networks.
In this comprehensive guide, we will delve into the installation, configuration, and practical usage of Aircrack-ng on Kali Linux. By the end of this article, you’ll be able to use Aircrack-ng to perform effective wireless security assessments.
What is Aircrack-ng?
Aircrack-ng is an 802.11 WEP and WPA/WPA2-PSK key cracking program. It focuses on different areas of Wi-Fi security:
-
Monitoring: Packet capture and export of data to text files for processing by third-party tools.
-
Attacking: Replay attacks, deauthentication, fake access points, etc.
-
Testing: Checking Wi-Fi cards and driver capabilities (monitor mode, injection).
-
Cracking: WEP and WPA PSK (WPA1 and WPA2).
It is important to note that Aircrack-ng should be used only on networks you own or have permission to test.
Installing Aircrack-ng on Kali Linux
Aircrack-ng is pre-installed in Kali Linux. However, to ensure the latest version, you can use the following commands:
To verify installation:
Understanding the Aircrack-ng Suite Components
Aircrack-ng is a suite composed of multiple tools:
-
airmon-ng – enables monitor mode on wireless interfaces.
-
airodump-ng – captures raw 802.11 frames.
-
aireplay-ng – injects frames (replay attacks, deauth, etc.).
-
aircrack-ng – cracks the WEP and WPA keys.
-
airbase-ng – creates rogue access points.
-
airserv-ng – allows remote packet injection.
-
packetforge-ng – forges packets.
-
ivstools – manipulates IVs.
-
wesside-ng – automatic WEP cracker.
-
tkiptun-ng – attack TKIP-based WPA networks.
Preparing Your System for Wireless Attacks
1. Enable Monitor Mode
This changes your interface from wlan0 to something like wlan0mon.
2. Kill Interfering Processes
Capturing Handshake Using Airodump-ng
Once in monitor mode, you can start listening to networks:
This lists all nearby Wi-Fi networks. Find your target network's BSSID and channel (CH).
Now, capture the WPA handshake:
Example:
This will save a .cap file that contains the captured handshake.
Deauthentication Attack Using Aireplay-ng
To speed up the handshake process, you can disconnect a client to force reauthentication:
You can also specify a client (optional):
Cracking WPA/WPA2 Password with Aircrack-ng
Now that you have the handshake file, you can crack it using a wordlist:
Popular wordlists:
-
rockyou.txt
-
crunch (for generating custom lists)
Example:
Creating Custom Wordlists with Crunch
You can create a custom wordlist using the crunch tool:
This creates all combinations of 8 to 12 characters using the given character set.
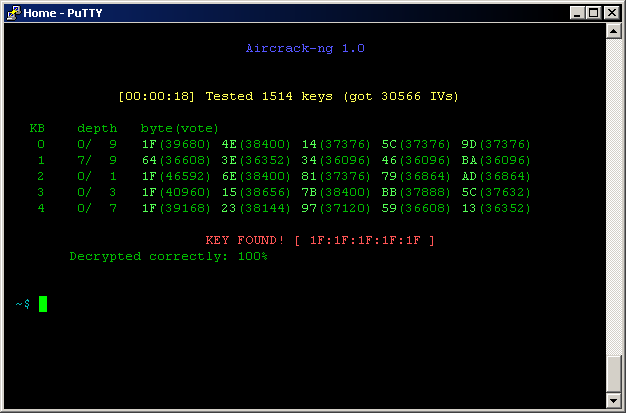
WEP Cracking with Aircrack-ng
Although WEP is outdated, here’s a basic example:
-
Capture packets:
-
Inject ARP requests:
-
Crack the WEP key:
Best Practices and Tips
-
Always scan channels separately for better packet capture.
-
Use an external Wi-Fi adapter that supports monitor mode and packet injection (e.g., Alfa AWUS036NHA).
-
Combine with tools like Wireshark for deeper analysis.
-
Use cowpatty, hashcat, or john for alternative cracking methods.
-
Keep your wordlists updated and relevant to target demographics.
Legal and Ethical Considerations
Performing wireless penetration tests without authorization is illegal in many jurisdictions. Always:
-
Have explicit permission from the network owner.
-
Avoid disrupting networks in public areas.
-
Use Aircrack-ng for education, research, or authorized testing only.
Conclusion
The Aircrack-ng suite is a robust set of tools that gives cybersecurity professionals the ability to audit and test the security of wireless networks. With components for monitoring, capturing, injecting, and cracking, it's an essential part of any ethical hacker’s toolkit.
Used responsibly and ethically, Aircrack-ng empowers you to understand Wi-Fi vulnerabilities and contribute to building more secure networks.